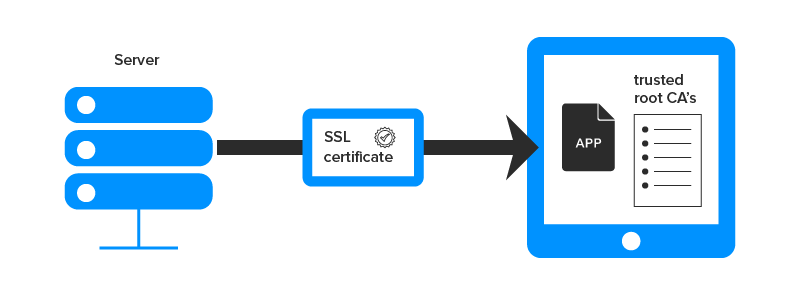
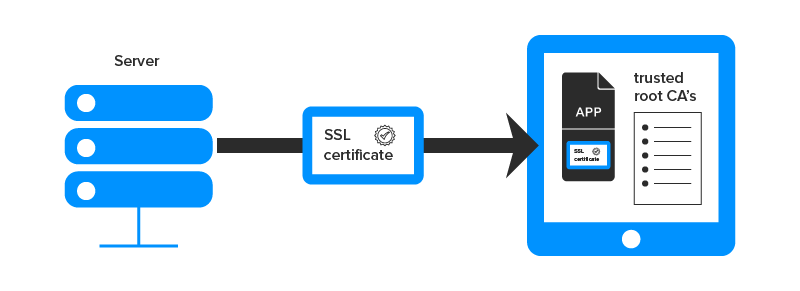
-
Let's Talk AI
Struggling to Be Seen Online?
Supercharge your marketing strategy
with Appinventiv Digital
Struggling to Be Seen Online?
Supercharge your marketing strategy
with Appinventiv Digital
-

How AI is Revolutionizing Data Governance for Enterprises and How to Do It Right?
-

AI in Biotech: 10 Proven Benefits and Use Cases That Are Transforming the Life Sciences Industry
-
How to Build An AI Trip Planner App? All You Need to Know
-

How AI is Empowering Clinicians with Smarter Decision-Making
-

10 Use Cases of AI in Nutrition and What It Takes to Build a Smart Diet Planning Platform
-
25+ Disruptive AI Agent Business Ideas You Should Launch in 2025
-

11 Ways AI is Transforming the Telemedicine Sector
-

How Agentic AI in Healthcare Is Bringing in Industry-level Transformation
-

How Much Does It Cost to Build an Advanced Driver Assistance System Like Tesla Autopilot?
-

10 Use Cases and Real Examples of How AI is Used in the Restaurant Industry
-
About
-
Services
IT Managed & Outsourcing
Consulting Services
Data Services
Didn't find what you're looking for? Let us know your needs, and we'll tailor a solution just for you. -
Industries
Didn't find what you're looking for? Let us know your needs, and we'll tailor a solution just for you.
-
Portfolio
-
Adidas
A leading digital platform to offer engaging shopping experience to users
-
KFC
A mobile app to digitalise & expand KFC’s digital footprint
-
Jobget
The MIT Innovation award-winning app withh $52 million funding reshaping the employment lanscape.
-
IKEA
A transforming ERP solution for the world’s largest furniture retailer
-
Domino's
A refined UX strategy for Domino's to increase their conversion rate by 23%
-
Edfundo
A SaaS-based financial literacy and smart money management platform for kids
-
-
Resources
- Blogs
- Guides
- Press Releases
Struggling to Be Seen Online?
Supercharge your marketing strategy
with Appinventiv Digital RECOMMENDED BlogsView All BlogsRECOMMENDED guidesView All Guides
RECOMMENDED BlogsView All BlogsRECOMMENDED guidesView All Guides
-
Generative AI in Manufacturing: 10 Popular Use-Cases
-

Mobile Apps: The Secret Ingredient of Better Health and Fitness
-

AR/VR in Construction – 10 Use Cases of How Augmented and Virtual Reality is Shaping the Industry
-
How Much Does It Cost to Build a Sports Betting App like Ladbrokes?
-

{Exclusive}: 6 Amazing Chatbot Design Strategy To Make your Bot an Interaction Ninja
-
How are Apps Like Draftkings & Fan Duel Changing the Sports Industry?